DNS Amplification Attack
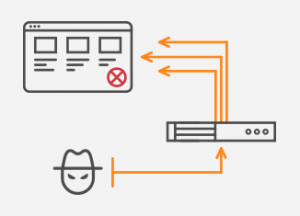 DNS Amplification attacks are a common type of Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in the domain name system (DNS). An attacker exploits these vulnerabilities by spoofing their IP address and sending queries to a vulnerable DNS server. These queries are subsequently turned into a much larger payload which are used to overwhelm the target server.
DNS Amplification attacks are a common type of Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in the domain name system (DNS). An attacker exploits these vulnerabilities by spoofing their IP address and sending queries to a vulnerable DNS server. These queries are subsequently turned into a much larger payload which are used to overwhelm the target server.
DNS Amplification is a reflection attack that takes advantage of publicly accessible and vulnerable DNS servers, causing them to flood a target server with large UDP packets. The amplification can be as large as 100x the size of the spoofed query, making for an overwhelming amount of data being sent to the target system.
Prevention and Mitigation
The best way to prevent DNS Amplification attacks is for everyone to do their part in correctly securing any publicly accessible DNS servers. The most common way of securing a DNS resolver and to ensure it’s not vulnerable is to make sure that it’s not accepting recursive queries from random IPs on the Internet. It should only accept recursive queries from specific IP prefixes only. Additionally, Service Providers can use ingress traffic filtering to filter out packets with spoofed source IPs.

